News Centerbarrow
Industry News
I7-6700k on the performance patch of KB4056892 patch by win 10
2019-05-27 23:15 The author:Administrator
This is the beginning of 2018, and Intel has a big story. According to foreign media reports, Intel processor there are serious loopholes in hardware level, and the hole is not through the microcode update, that is to say, unless the change don't have the defects of the CPU, otherwise can not fundamentally solve the problem.

But the bigger problem is that the bug involves almost all Intel X86 processors in the last 20 years, which means that there are no users who are currently using Intel cpus.
The vulnerability was widespread, including Intel cpus and Windows, Linux and Mac OS systems. Through holes, third-party applications can get extremely important kernel data in memory, and the holes at the same time when 2 (official named Meltown and Spectre), the situation is very serious.

Meltown and Spectre
According to the known information, the Meltown vulnerability seems to be the only one in Intel, while the Spectre vulnerability covers most of the CPU chips of Intel, AMD and ARM, which means that all computer phones are not immune. Fortunately, the exploit cost of the Spectre vulnerability is very high, so the risk is not as big as Meltown.
Will closing loopholes cause 30% performance damage?
For the average user, what is the impact of a bug that doesn't care? Only, as a result of this vulnerability is CPU architecture design problem, although the Linux, Windows have to solve this problem in the form of system update (KB4056892 update), but at the same time the CPU performance will decline 5% to 30%.
30 percent performance loss, wouldn't it let the CPU power go back to liberation overnight? But don't worry about it. According to the actual test, the biggest impact is the frequent application environment, so the biggest impact should be the database server of the major companies. For general users (including games, office, graphic design, video production, 3D modeling, etc.), the impact should be very small.
Before and after the update CPU measured contrast.
Mouth says, of course, we use an Intel Core i7 6700 k, 32 gb DDR4 carrying 2400 memory and a 500 gb samsung 850 EVO SSD test, mainly contrast before and after the system upgrade CPU, cache and memory performance, solid-state hard disk read and write performance differences.
The test was based on Windows 10 KB4056892 update.
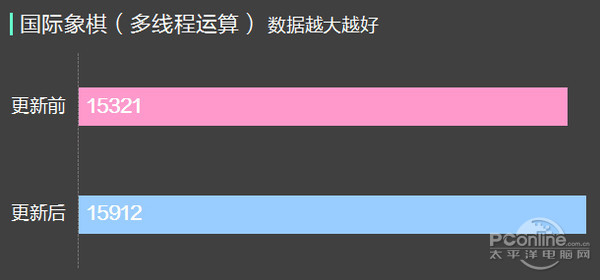
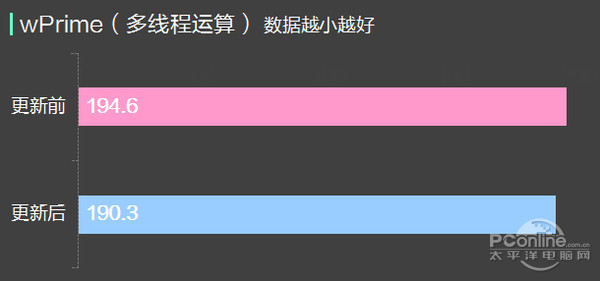
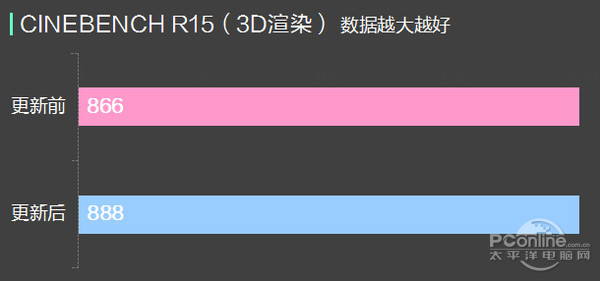
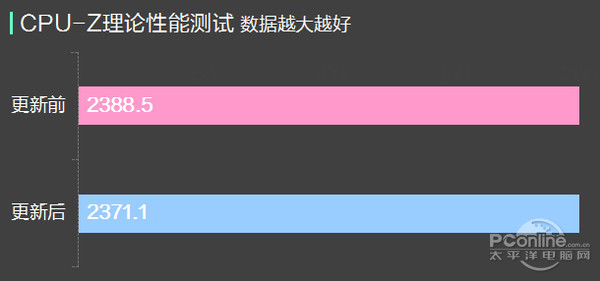
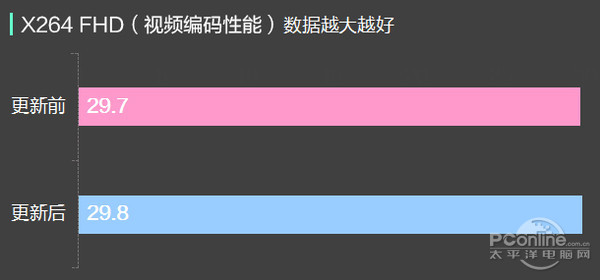
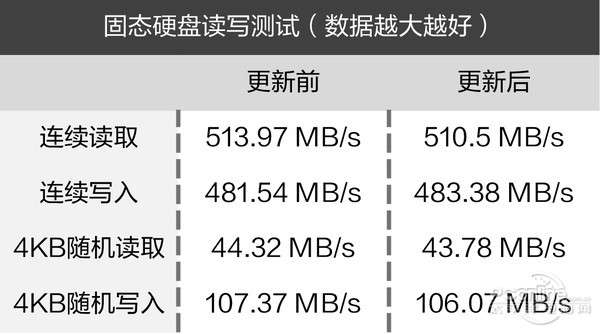
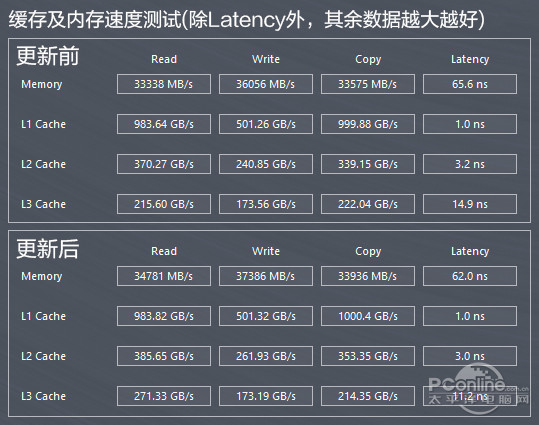
Can be seen from the test, before and after the update KB4056892, CPU, memory, and the performance of the SSD had no obvious change, data access can be thought of in the error range, so the update for this hardware platform we hand no significant influence.
Of course, since we only tested the CPU of i7 6700K, it is not natural to represent all Intel CPU products. However, according to the self-test results of online users, the hardware performance of KB4056892 has not been significantly reduced.
However, the Windows update 10 patches only for Meltown this vulnerability, and a broader impact the Spectre of vulnerability remains unresolved, in the next update will affect system and hardware performance, is still unknown.

Finish see test results, you can feel free to update the system, at present the two holes on the system of information security hazard is very serious, recommend to update during this time, we will also pay close attention to the situation.
Patch download link: https://www.sysgeek.cn/kb4056892/
News from:太平洋电脑网

